Defense Technologies
- Dot AI / AI Workflow Automation
- Pulse / AI News Intelligence
- Dispatch / Office Automation System
- Bit / Business Intelligence Tool
- L2 / Layer Two Switch
- CC / Communication Controller
- Scan / Software Defined Radio
- Radex / Radar Data Extractor
- mDC / Mobile Data Center
- sSA / Solid State Autoloader
- eMIA / Private Enterprise Resource Planning
- Trail / Covert Supply Chain Management
- Ozone / Airspace Management System
- Listen / Lawful Interception System for Tracking, Evaluation & Notification
- Deep Sight / Deep Packet Inspection
- Chameleon / Secure Keyboard
- Minute Chameleon / Secure Display
- Pocket Chameleon / Secure Mobile
Mission-critical technologies,
built for the battlefield.
Operational Capabilities and Strategic
Engagements in the Defense Sector
15
Products & Services
242
08
Mission-critical National Initiatives
11
Patents
Products & Services
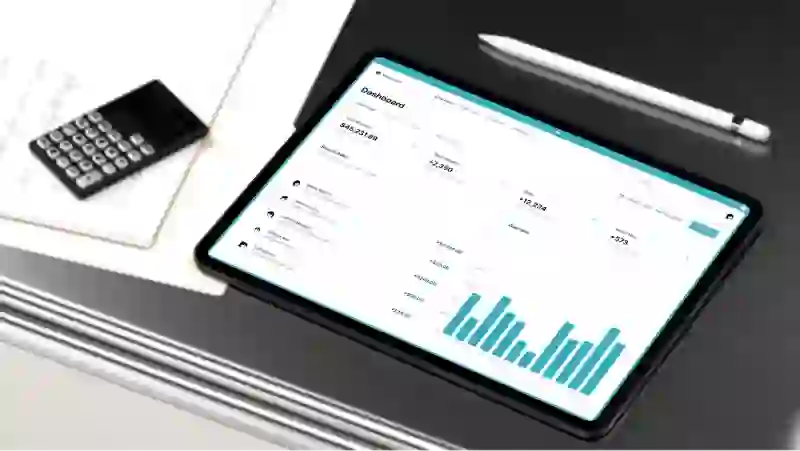
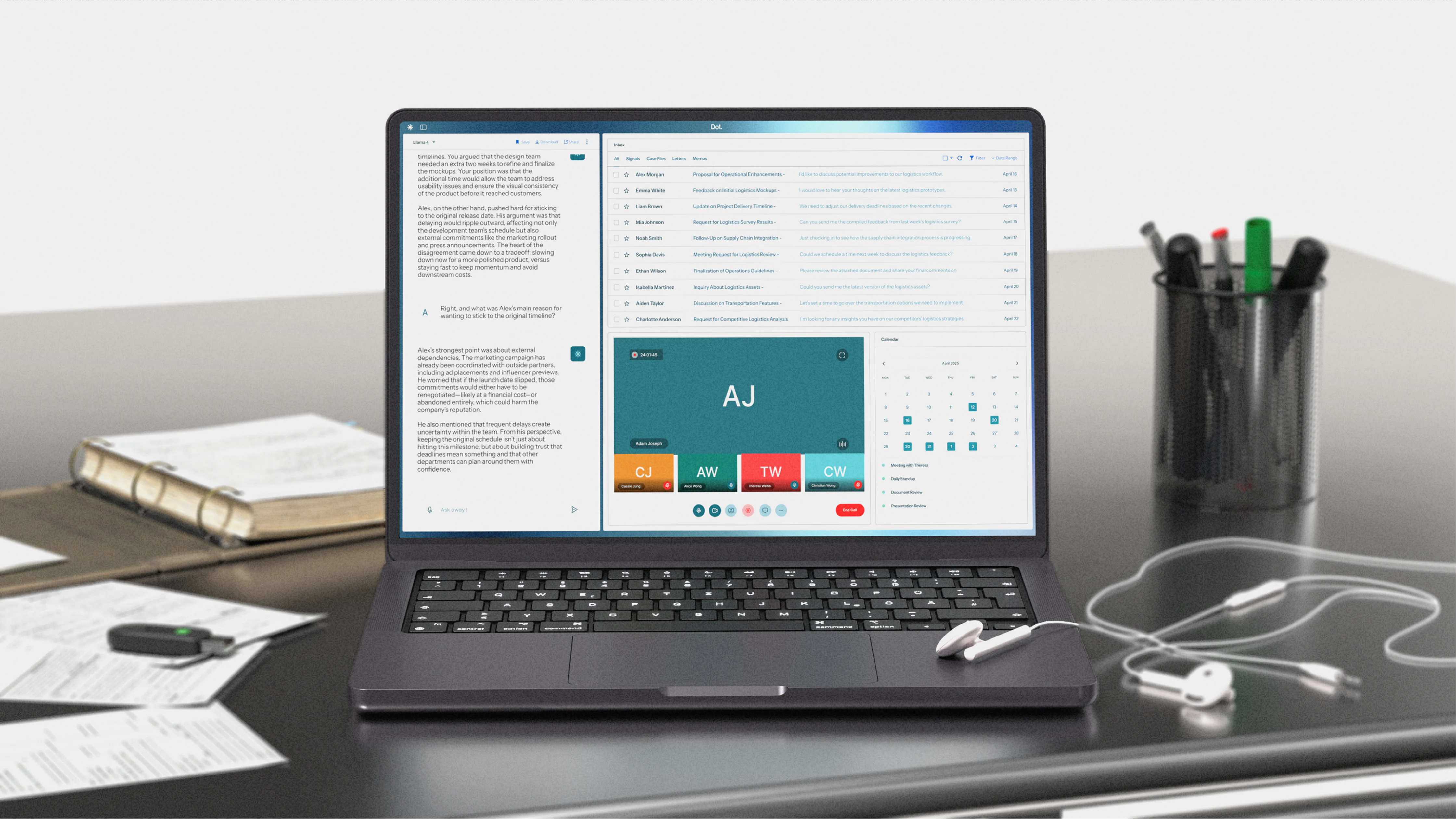
01
Dot AI
AI Workflow Automation
sw

DotAI brings Large-Language-Model power behind the firewall—giving enterprises a multimodal co-pilot that drafts, answers, retrieves, and records with the security, compliance, and ownership they demand.
a.
Multimodal reasoning core
b.
Perpetual, one-time licence
c.
Air-gapped, on-prem deployment
d.
Encrypted storage & governance
e.
GDPR & HIPAA compliance toolkit
f.
Horizontally & vertically scalable framework
g.
Generative content suite
h.
Conversational knowledge retrieval
i.
Meeting capture & insight generator
02
Pulse
AI News Intelligence
sw
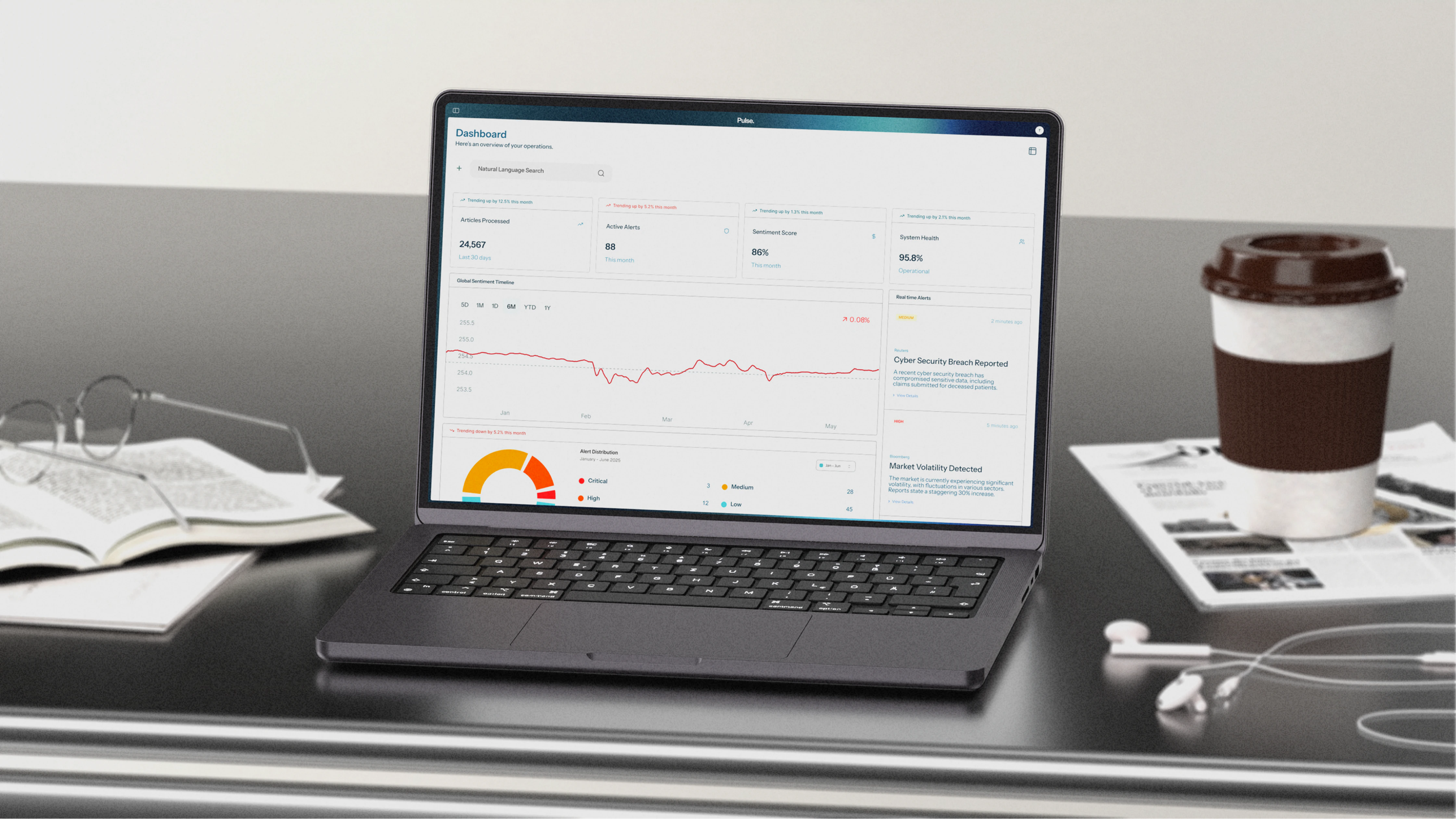
Ingests global news at scale, turns raw articles into machine-searchable knowledge, and delivers realtime alerts, sentiment/bias analytics, and executive-ready reports—running on customer-controlled infrastructure for sovereignty and reliability.
a.
Multi-source collection fabric
b.
RDB to VDB knowledge pipeline
c.
Natural-language query system
d.
LLM sentiment & bias analytics
e.
Alerting & triggers
f.
Reporting & visualization
g.
Person & image intelligence
h.
Sovereign, scalable infrastructure
i.
Continuous monitoring & ops
j.
Road-mapped deployment
03
Dispatch
Office Automation System
sw
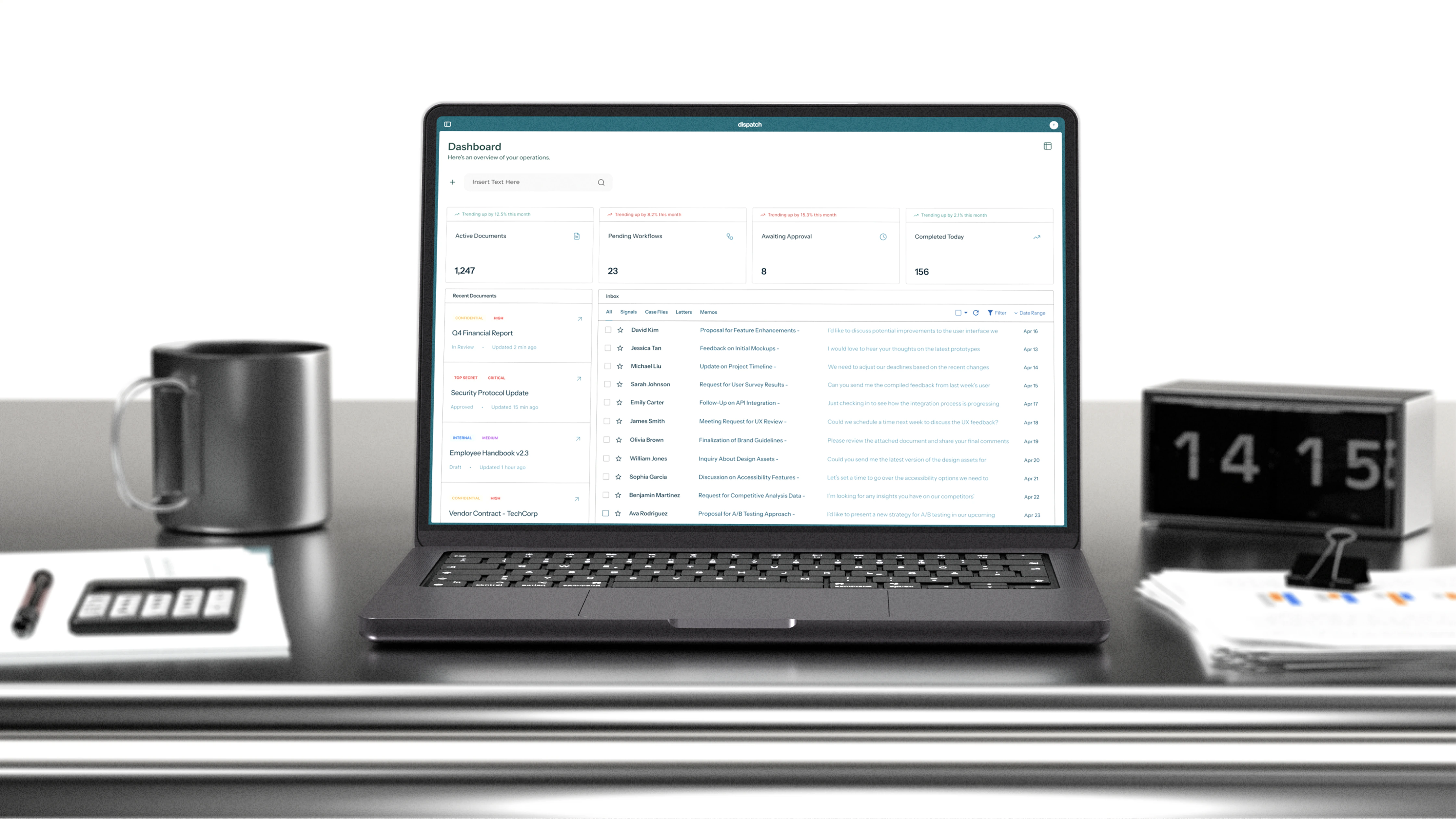
An enterprise-grade Office Automation System engineered to accelerate decision cycles while meeting the most rigorous governance and security requirements.
a.
Encrypted intra-org correspondence
b.
Visual workflow automation
c.
Real-time configurable watermarks
d.
ERP-ready integration layer
e.
Policy-based archiving
f.
Inline annotation & remarks
g.
Web-native authoring & viewer
h.
Role-driven print & audit controls
i.
Class & precedence routing
04
Bit
Business Intelligence Tool
sw
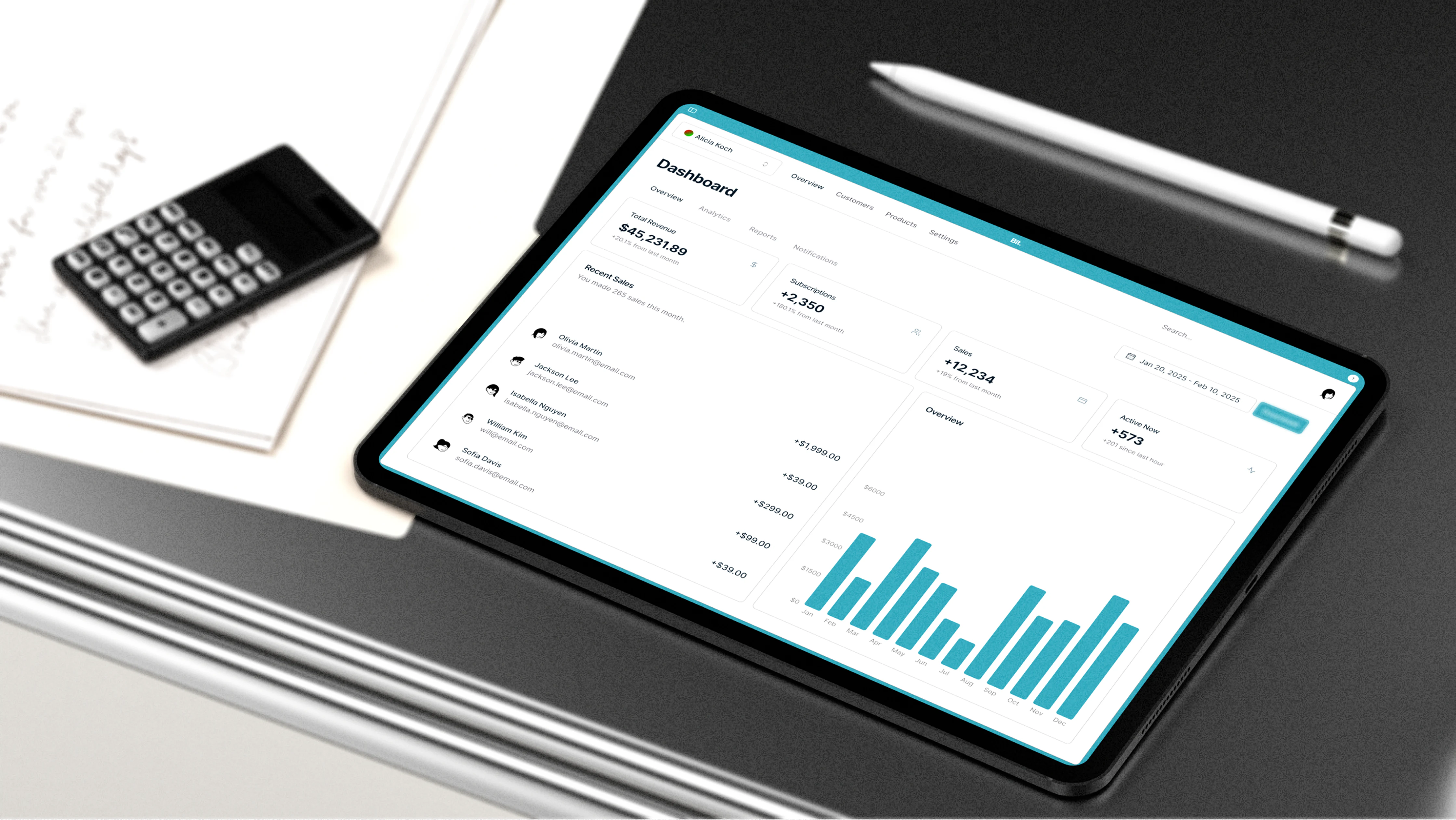
A demand-forecasting solution that fuses data engineering, advanced machine learning, and decision visualization into one governed environment which allows operations, finance, and supply-chain teams to plan with confidence.
a.
Unified data pipeline
b.
Industrial-strength ML engine
c.
API-first architecture
d.
Continuous prediction service
e.
Embedded analytics & visualization
f.
Scalable & automation-ready
05
L2
Layer Two Switch
hw/sw

Delivers secure, deterministic Layer 2 connectivity for mission-critical deployments from tactical field units to industrial control rooms without compromising on manageability or size, weight, and power (SWaP) constraints.
a.
Hardened, dual-range power subsystem
b.
High-density copper + fiber fabric
c.
Military-grade I/O placement
d.
Intelligent Layer 2 services
e.
GUI-driven configuration
f.
Scalable, standards-aligned design
06
CC
Communication Controller
hw/sw

A single, resilient overlay, automatically selecting the optimum path for every packet. Field-proven for more than a decade and protected by U.S. patents, it delivers assured connectivity wherever conventional networks falter.
a.
Self-forming architecture
b.
Self-healing intelligence
c.
Multi-link agility
d.
Node-level adaptability
e.
Source-node encryption
f.
Integrated data-distribution service
07
Scan
Software Defined Radio
hw/sw

A software-defined radio combining high-performance DSPs, FPGAs, and wideband RF front-ends in a programmable package—delivering secure, jam-resistant voice and data links that can be re-tuned in the field with new waveforms.
a.
Multi-band waveform agility
b.
Anti-jam frequency hopping
c.
Integrated voice & data link
d.
Adaptive slot MAC
e.
Modular RF integration
f.
MELP speech compression
g.
TRANSEC / COMSEC & Red-Black isolation
h.
Network management & dev kit
08
Radex
Radar Data Extractor
hw/sw

Converts raw returns from mixed-generation surveillance radars into a single, digital track picture making it ready for immediate display on local consoles and for fusion with data from other sensors at upper-tier command systems.
a.
Mobile-agent interfaces
b.
Analogue track extraction
c.
Multi-radar correlation
d.
Real-time visualization
e.
Scalable, standards-aligned design
09
mDC
Mobile Data Center
hw/sw

A self-contained, vehicle-borne command-and-control platform with modular subsystems for expeditionary air-defense operations—delivering datacenter-class computing and resiliency wherever the mission demands.
a.
Ruggedized, low-SWaP chassis
b.
Integrated Communication Controller
c.
Extended temperature envelope
d.
Redundant Ethernet fabric
e.
Pre-hardened Linux stack
f.
Scalable compute & storage pods
g.
Energy-efficient design
10
sSA
Solid State Autoloader
hw/sw

A replacement for legacy electromechanical relays with ruggedized power electronics, delivering faster, safer, and more reliable round-chambering for main battle tanks.
a.
All–solid-state switching
b.
Digital operator display
c.
Smart memory & sensing module
d.
High-current circuitry
e.
Combat-proven pedigree
11
eMIA
Private Enterprise Resource Planning
sw

A mission-ready Enterprise Resource Planning and Manufacturing Execution System engineered for defense ministries, primes, and depots that cannot compromise on data sovereignty or cyber resilience.
a.
Sovereign, on-premise deployment
b.
Zero-trust security architecture
c.
Need-to-know access control
d.
Immutable audit & compliance
e.
Disconnected & contested-edge operation
f.
Defense logistics & codification
g.
Depot MRO & MES
h.
Program-centric finance & contracts
i.
Interoperability & data portability
12
Trail
Covert Supply Chain Management
sw

An end-to-end digital backbone for materiel readiness—tracking assets, routing orders through secure channels, integrating with ERP and C2 systems, and preserving an immutable audit trail.
a.
Defense Catalogue & NSN Registry
b.
Readiness-Focused Material Requirement Planner
c.
Secure Sourcing & Offset-Compliance Suite
d.
Supplier Relationship & Vetting Management
e.
Multi-Tier Coordination & Data-Integration Network
f.
Logistics Command & Dynamic Routing Engine
g.
Depot / Warehouse & Armory Management
h.
Tactical Tracking & Identification
i.
Immutable Audit Logging & Chain-of-Custody
13
Ozone
Airspace Management System
sw

A nation-scale command-and-control layer that fuses airborne sensors, evaluates threats in real time, assigns defensive assets, and keeps controllers fully informed—even when components fail.
a.
Multi-sensor fusion core
b.
Threat Evaluation & Weapon Assignment (TEWA)
c.
Post-raid & readiness analytics
d.
Integrated radar-data extractors
e.
Cognitive communication controller
f.
Air–ground situational gateway
g.
Fault-tolerant C2 architecture
h.
Built-in disaster-recovery workflows
14
Listen
Lawful Interception System for Tracking, Evaluation & Notification
sw

Provides a single, policy-driven environment for filtering, collecting, analysing, and securely storing voice and data traffic across every major communications network.
a.
Multi-network capture fabric
b.
Elastic subscriber scaling
c.
Multi-agency tenancy
d.
Cross-provider interception
e.
Advanced analytics & reporting
f.
Inter-agency data exchange
g.
Comprehensive session monitoring
h.
Hardened, future-proof architecture
15
Deep Sight
Deep Packet Inspection
sw

Equips national cyber-defense teams with line-rate inspection, policy enforcement, and intelligence extraction across carrier-scale links—shielding critical infrastructure from advanced threats while preserving network performance and availability.
a.
100 Gbps inspection fabric
b.
High-speed URL blocker
c.
Elastic, modular architecture
d.
Rich metadata extraction
e.
Policy-driven enforcement APIs
f.
On-premises sovereignty
16
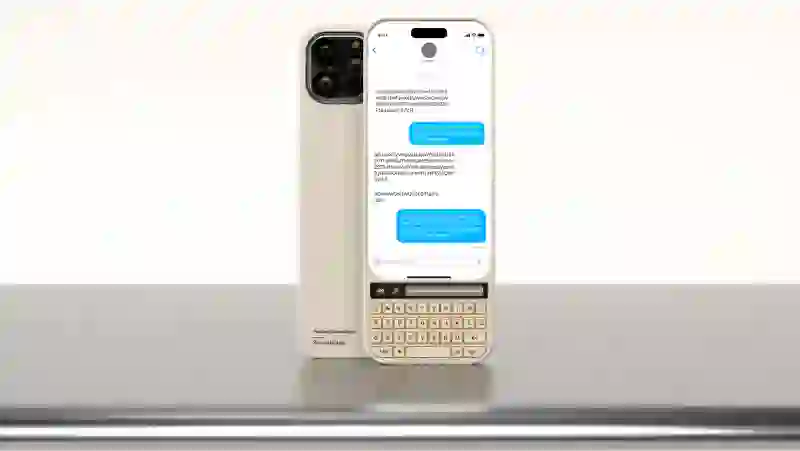
Chameleon
Secure Keyboard
hw/sw

Looks and feels like an ordinary desktop keyboard, yet every keystroke is encrypted before it reaches the host or network. A built-in display allows plaintext composition locally while outbound data remains ciphertext.
a.
Realtime keystroke encryption
b.
Application-agnostic compatibility
c.
Red/Black path isolation
d.
Tamper-responsive chassis
e.
Clipboardswitch safeguard
f.
Multilanguage Unicode support
g.
Enterprise key-management suite
17
Minute Chameleon
Secure Display
hw/sw

Encrypts each keystroke in real time before it reaches the OS, application, or network. Resembling an ordinary desk clock, it sits between the keyboard and host—showing cleartext locally while keeping all outbound data encrypted.
a.
Realtime keystroke encryption
b.
Application-agnostic compatibility
c.
Red/Black path isolation
d.
Tamper-responsive chassis
e.
Clipboardswitch safeguard
f.
Multilanguage Unicode support
g.
Enterprise key-management suite
18
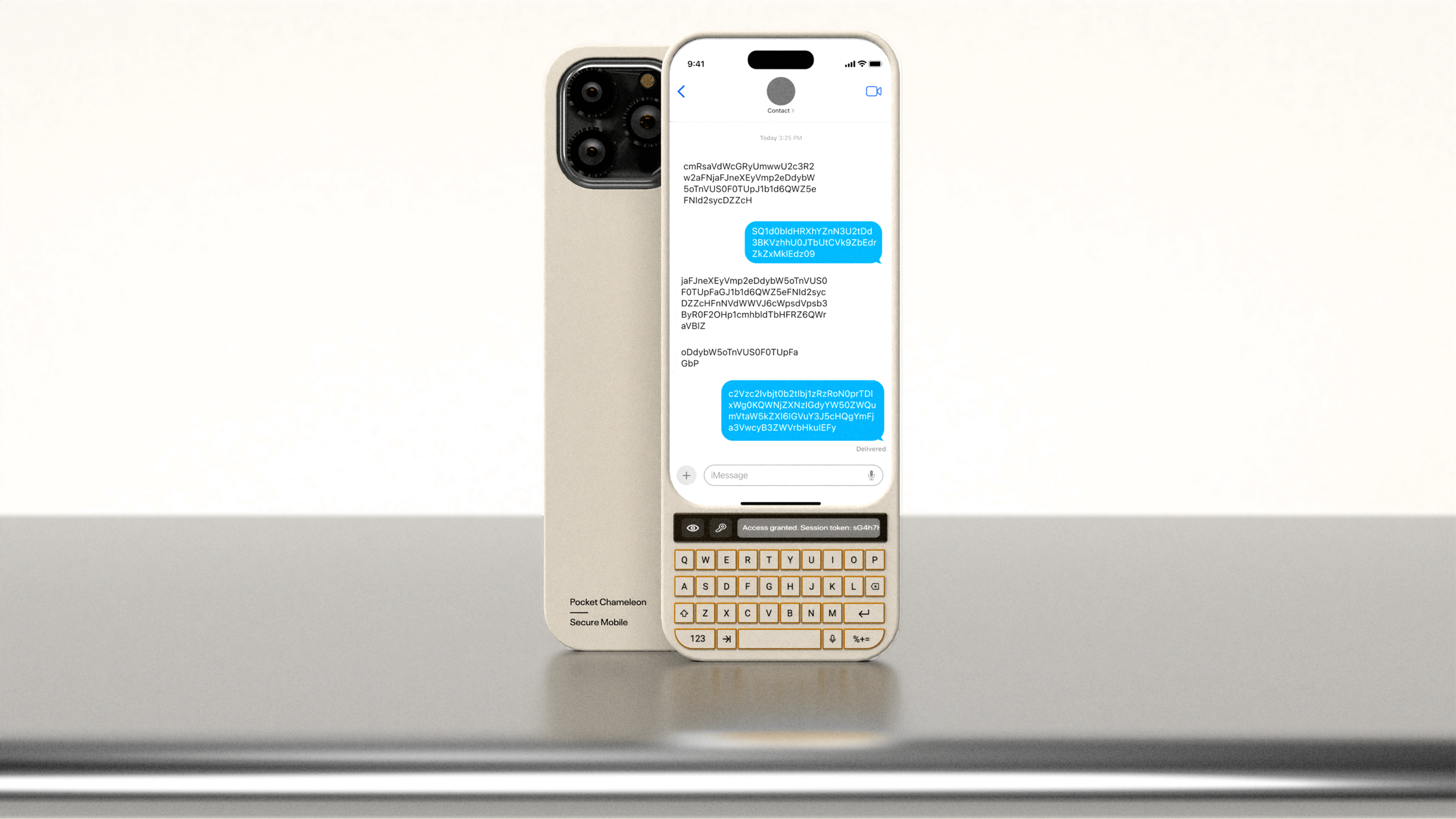
Pocket Chameleon
Secure Mobile
hw/sw