Busniess Technologies
- Dot AI / AI Workflow Automation
- Pulse / AI News Intelligence
- Optimal / Enterprise Resource Planning
- Dispatch / Office Automation System
- Bit / Business Intelligence Tool
- Sentt / Smart Ecosystem for Networked Transportations & Tracking
- Chameleon / Secure Keyboard
- Minute Chameleon / Secure Display
- Pocket Chameleon / Secure Mobile
Enterprise solutions,
secure by design.
Operational Capabilities and Strategic
Engagements in Business Tech
09
Products & Services
Products & Services
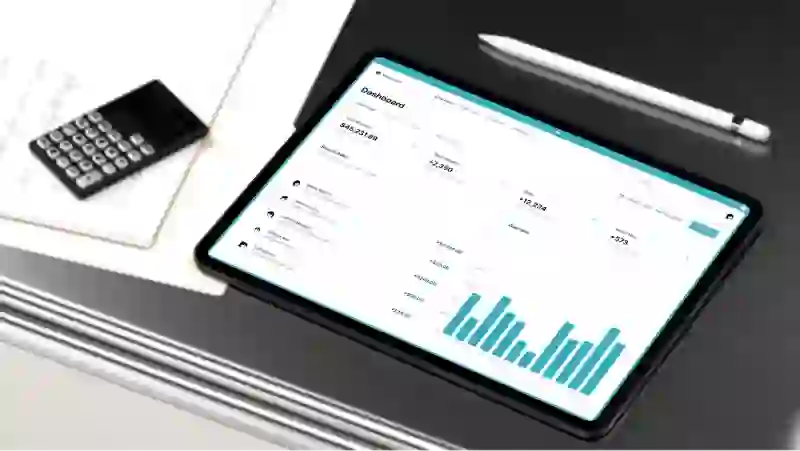
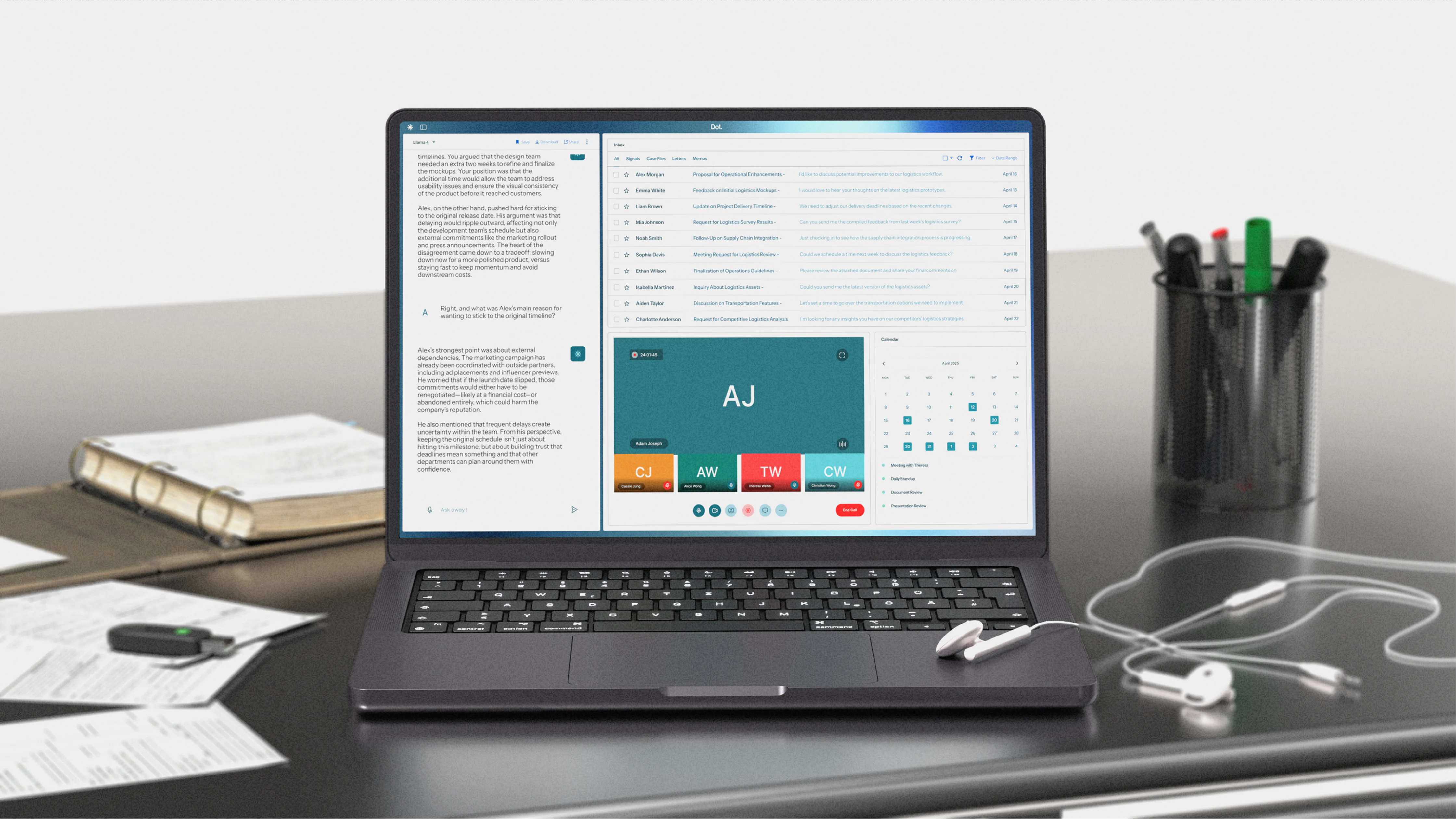
01
Dot AI
AI Workflow Automation
sw

DotAI brings Large-Language-Model power behind the firewall—giving enterprises a multimodal co-pilot that drafts, answers, retrieves, and records with the security, compliance, and ownership they demand.
a.
Multimodal reasoning core
b.
Perpetual, one-time licence
c.
Air-gapped, on-prem deployment
d.
Encrypted storage & governance
e.
GDPR & HIPAA compliance toolkit
f.
Horizontally & vertically scalable framework
g.
Generative content suite
h.
Conversational knowledge retrieval
i.
Meeting capture & insight generator
02
Pulse
AI News Intelligence
sw
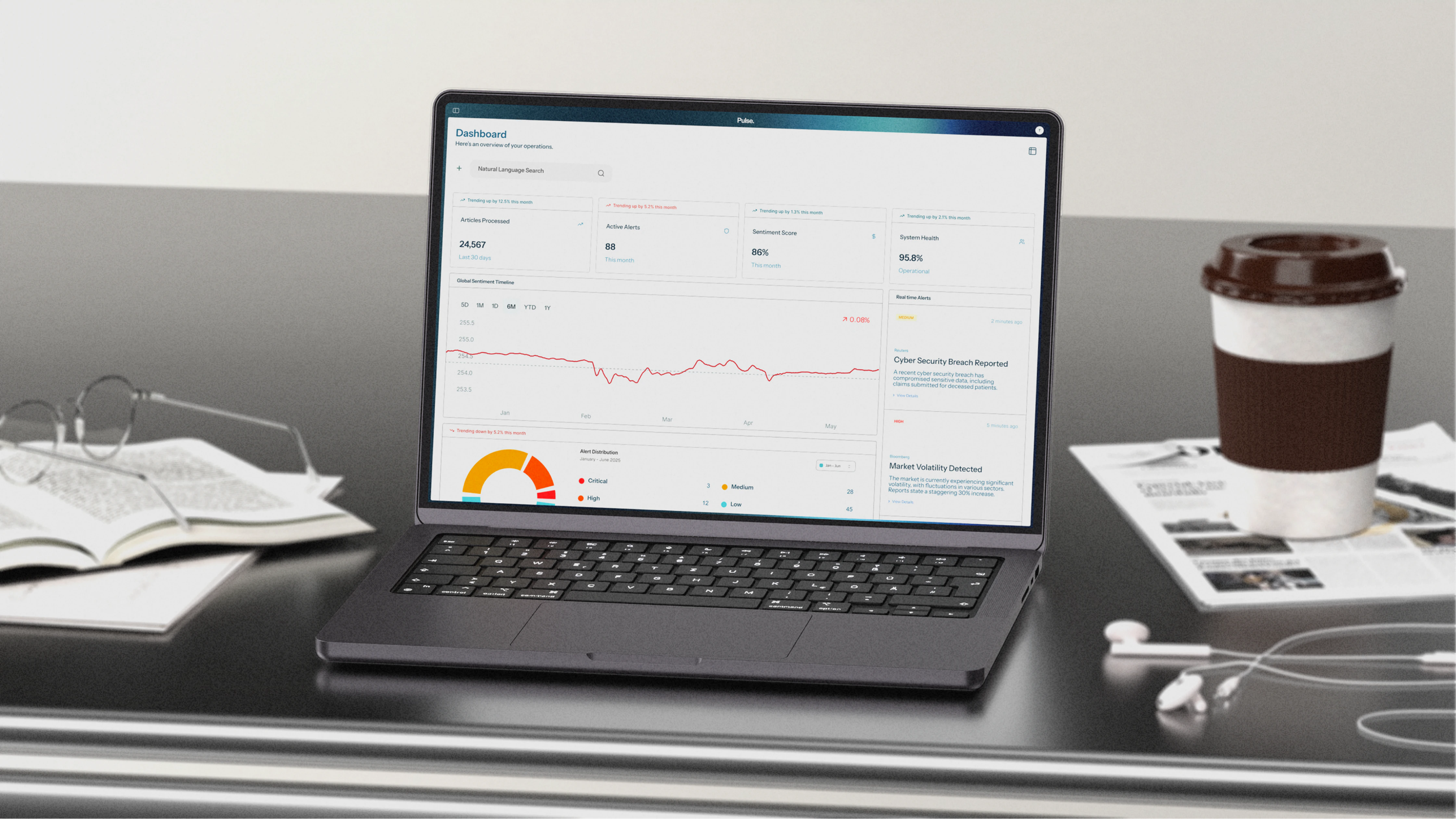
Ingests global news at scale, turns raw articles into machine-searchable knowledge, and delivers realtime alerts, sentiment/bias analytics, and executive-ready reports—running on customer-controlled infrastructure for sovereignty and reliability.
a.
Multi-source collection fabric
b.
RDB to VDB knowledge pipeline
c.
Natural-language query system
d.
LLM sentiment & bias analytics
e.
Alerting & triggers
f.
Reporting & visualization
g.
Person & image intelligence
h.
Sovereign, scalable infrastructure
i.
Continuous monitoring & ops
j.
Road-mapped deployment
03
Optimal
Enterprise Resource Planning
sw

Optimal is a full-spectrum Enterprise Resource Planning and Manufacturing Execution System engineered for organizations that refuse to trade data sovereignty for digitization. Deployed entirely on your own infrastructure inside your firewall or private cloud it delivers the analytics, traceability, and automation typical of large, cloud-hosted suites while keeping every byte under your direct control.
a.
Modular, pick-and-choose architecture
b.
On-premise deployment & database independence
c.
End-to-end traceability via RFID / NFC & IoT
d.
Proprietary encryption & granular roles
e.
AI-powered business intelligence
f.
Open-edge integration
g.
Comprehensive reporting & logging
04
Dispatch
Office Automation System
sw
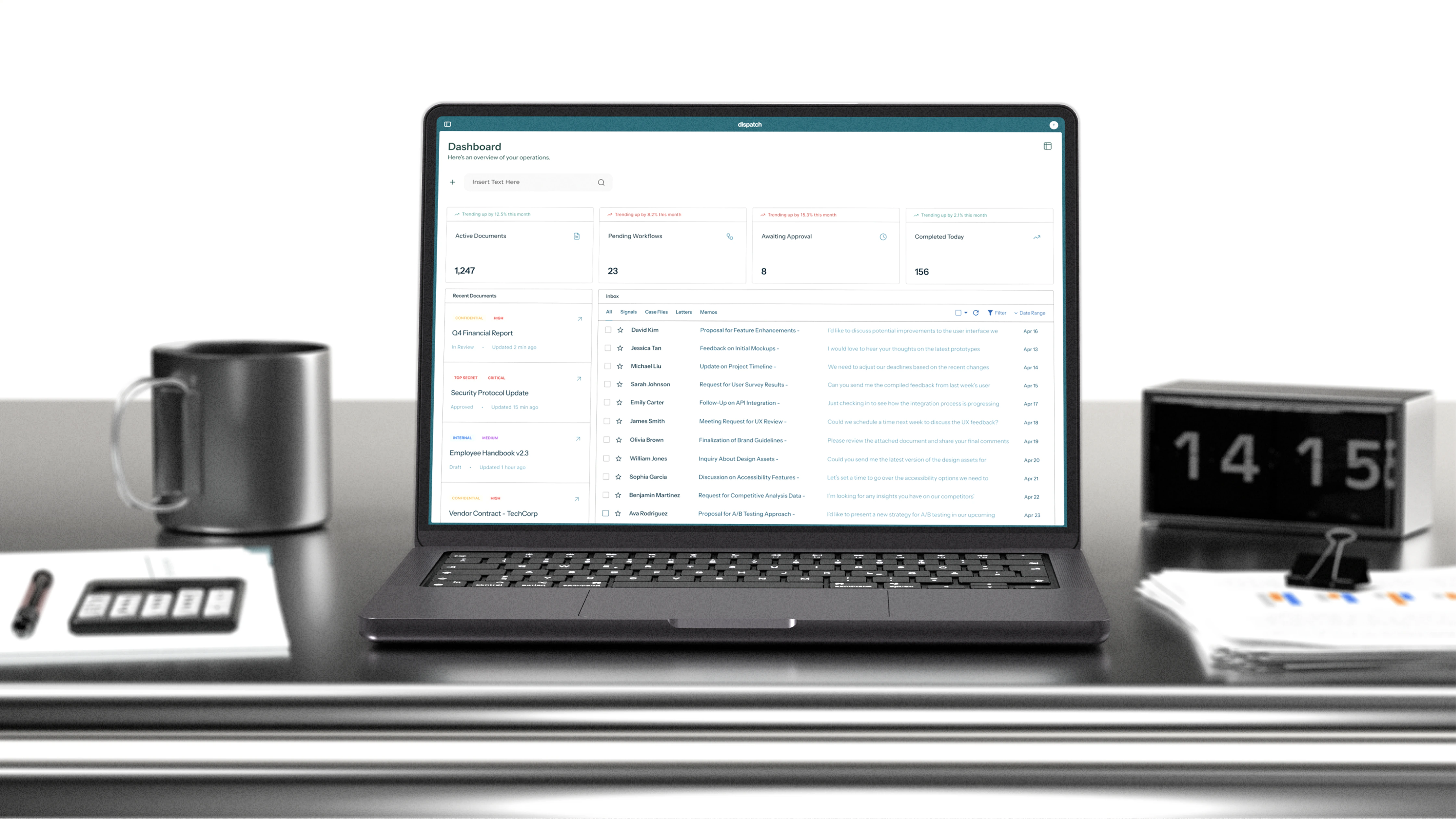
An enterprise-grade Office Automation System engineered to accelerate decision cycles while meeting the most rigorous governance and security requirements.
a.
Encrypted intra-org correspondence
b.
Visual workflow automation
c.
Real-time configurable watermarks
d.
ERP-ready integration layer
e.
Policy-based archiving
f.
Inline annotation & remarks
g.
Web-native authoring & viewer
h.
Role-driven print & audit controls
i.
Class & precedence routing
05
Bit
Business Intelligence Tool
sw
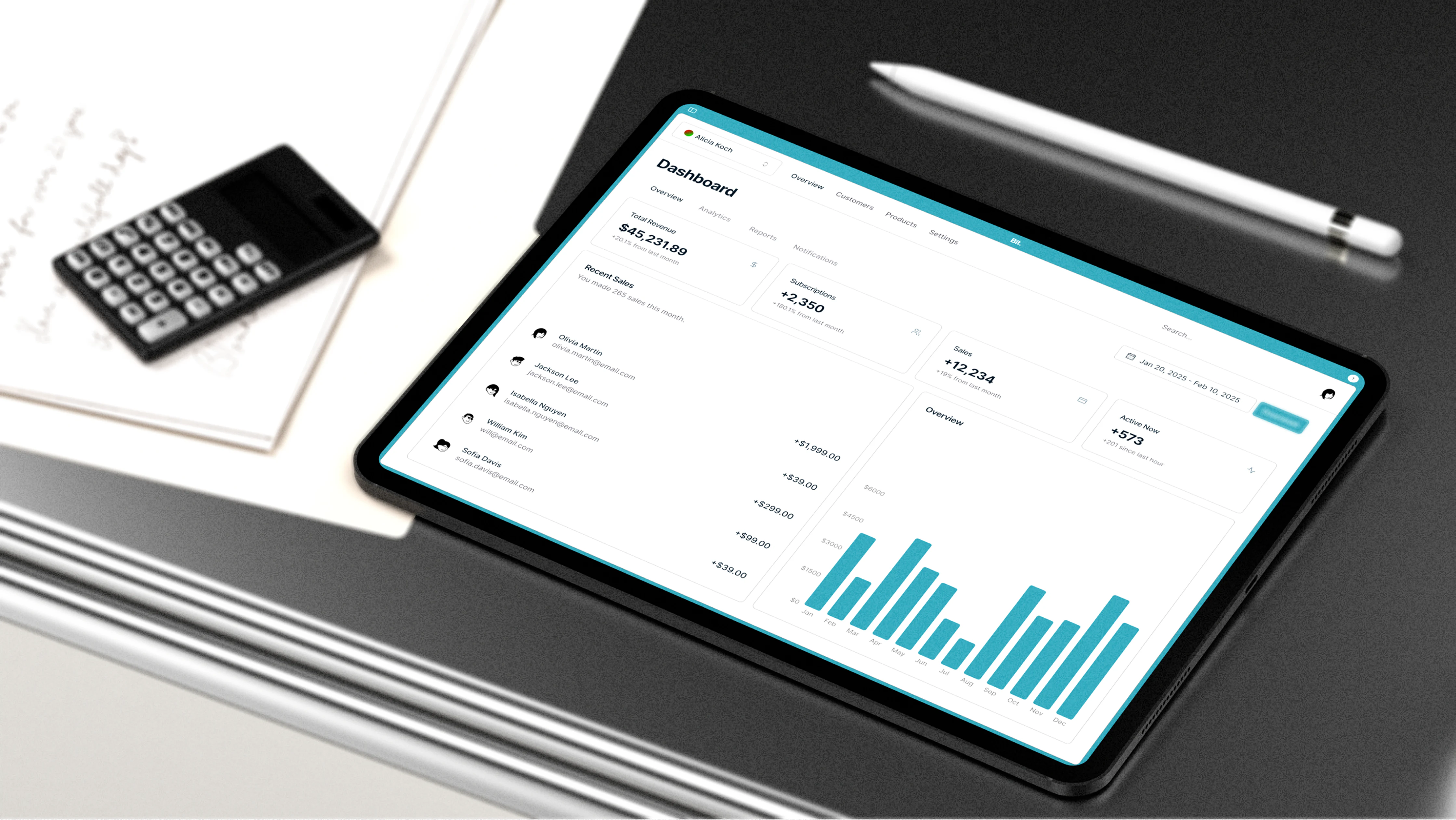
A demand-forecasting solution that fuses data engineering, advanced machine learning, and decision visualization into one governed environment which allows operations, finance, and supply-chain teams to plan with confidence.
a.
Unified data pipeline
b.
Industrial-strength ML engine
c.
API-first architecture
d.
Continuous prediction service
e.
Embedded analytics & visualization
f.
Scalable & automation-ready
06
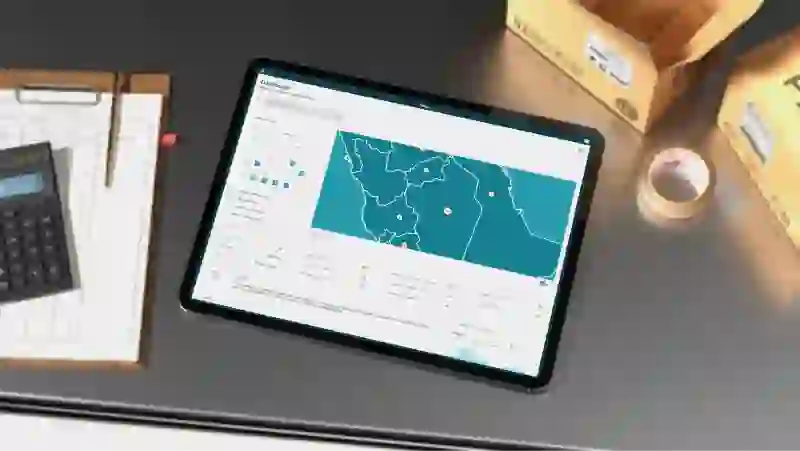
Sentt
Smart Ecosystem for Networked Transportations & Tracking
sw

Connects suppliers, carriers, warehouses, and storefronts into a single logistics backbone—streamlining planning, sourcing, transportation, and fulfillment for efficiency and transparency.
a.
Product Catalogue & Master Data
b.
MRP & Demand Planning
c.
Sourcing Suite
d.
Supplier Relationship Management
e.
Supplier Collaboration Network
f.
Transportation Management (TMS)
g.
Warehouse & Yard Management (WMS/YMS)
h.
Auto-ID & IoT Tracking
i.
Inventory Management & OMS
07
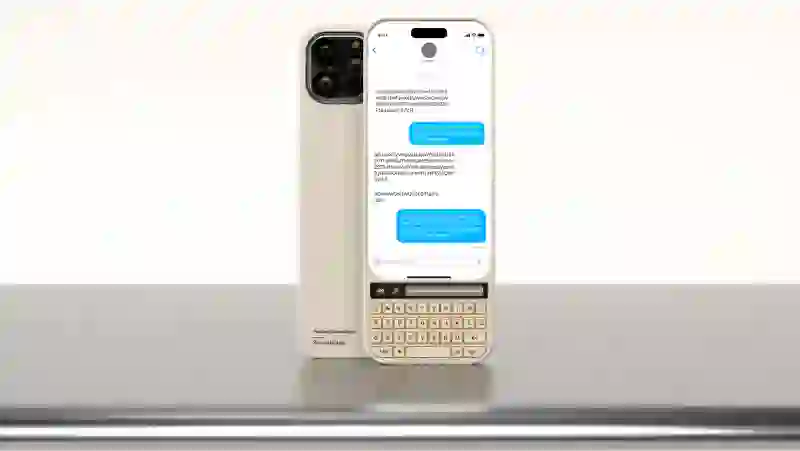
Chameleon
Secure Keyboard
hw/sw

Looks and feels like an ordinary desktop keyboard, yet every keystroke is encrypted before it reaches the host or network. A built-in display allows plaintext composition locally while outbound data remains ciphertext.
a.
Realtime keystroke encryption
b.
Application-agnostic compatibility
c.
Red/Black path isolation
d.
Tamper-responsive chassis
e.
Clipboardswitch safeguard
f.
Multilanguage Unicode support
g.
Enterprise key-management suite
08
Minute Chameleon
Secure Display
hw/sw

Encrypts each keystroke in real time before it reaches the OS, application, or network. Resembling an ordinary desk clock, it sits between the keyboard and host—showing cleartext locally while keeping all outbound data encrypted.
a.
Realtime keystroke encryption
b.
Application-agnostic compatibility
c.
Red/Black path isolation
d.
Tamper-responsive chassis
e.
Clipboardswitch safeguard
f.
Multilanguage Unicode support
g.
Enterprise key-management suite
09
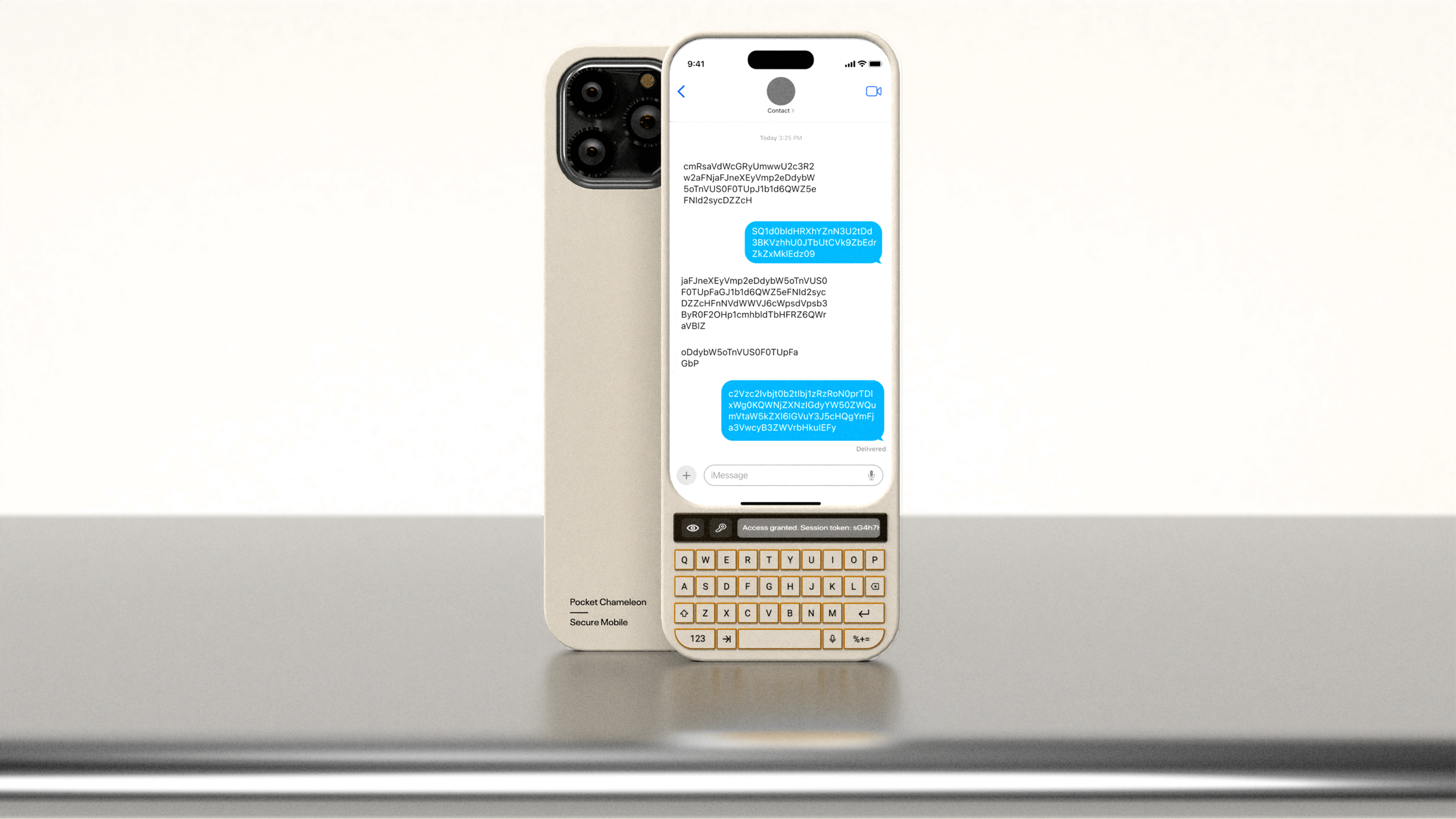
Pocket Chameleon
Secure Mobile
hw/sw